
But for those seeking privacy, freedom of expression, or simply a glimpse into this hidden world, the Dark Web is a fascinating, albeit dangerous, place to explore. Cryptocurrency, particularly Bitcoin, plays a significant role on the Dark Web. Many transactions conducted on the Dark Web involve the exchange of cryptocurrencies, as they offer a level of anonymity that traditional currencies cannot.
Best Dark Web Sites
I found it especially useful for testing new services without risking my main email address, though messages expire after 24 hours. It’s also important to note that your activities on the dark web aren’t completely immune to web tracking, and the expectation of anonymity can create a false sense of security. You can run a dark web scan to see if any of your data has leaked onto the black market.
This is a blog with cybersecurity tips created by the Electronic Frontier Foundation (EFF), a popular non-profit that specializes in digital privacy. The blog contains tons of useful guides about how you can avoid online surveillance. SecureDrop is an open-source submission system that nonprofit organizations (NGOs), journalists, and news organizations can use to share and receive sensitive files securely.
What Kind Of Content Can I Find On The Dark Web?
The CIA (Central Intelligence Agency) provides a .onion version of its website, enabling individuals to bypass restrictions to access its content from anywhere. This platform allows visitors to anonymously explore the World Factbook, submit information, apply for jobs, and perform any other actions available on the CIA’s main site. While Tor offers anonymity by routing your traffic through a decentralized network of nodes (onion routing), it shouldn’t be your only line of defense for privacy. Malicious actors and government agencies can run Tor nodes, compromising privacy and security. In fact, there have been instances where attackers controlled hundreds of Tor nodes. The Deep Web includes unindexed content like private databases and password-protected sites accessible with standard browsers.

However, you can still take illegal actions within Tor that could incriminate you regardless of the browser’s legality. You could easily use Tor in an attempt to pirate copyrighted content from the deep web, share illegal pornography, or engage in cyber terrorism. Using a legal browser will not make your actions fall to the right side of the law. Venturing further into the deep web does bring a bit more danger to the light. For some users, portions of the deep web offer the opportunity to bypass local restrictions and access TV or movie services that may not be available in their local areas.
Risks And Dangers Of The Dark Web
I personally recommend Tor over VPN because it’s the safer option — the VPN encrypts your traffic and changes your IP address, so the Tor network can’t see them. That’s helpful because Tor can suffer IP leaks and malicious actors can run Tor servers. Basically, if a Tor IP leak occurs before you connect to the VPN, your real IP address will be exposed. But if you connect to the VPN before connecting to Tor and an IP leak occurs, only the VPN’s IP address will be exposed. Yes, but you need to be cautious because there are many malicious sites on the dark web. The best way to do that is to get the link from legitimate sources, like The Hidden Wiki.

Encrypted Communication Tools
I strongly advise doing your own research to make sure you’re not breaking any local laws by visiting the dark web. Also, even in countries where accessing the dark web is legal, it’s still against the law to use or host sites that promote criminal activities. Torch is one of the oldest dark web search engines, and it’s generally considered one of the safest. It has some advertisements on its home page, but they’re for popular searches and services to help get you started.
The Scale And Popularity Of DDoS-for-hire Services Is On The Up
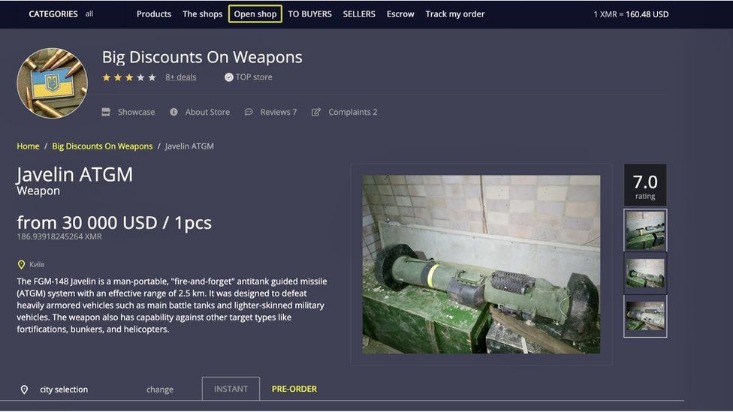
Illegal marketplaces are merely a small fraction of what’s actually there. When the dark web is mentioned online, it is usually in tandem with criminal marketplaces and arrests made by law enforcement agencies. Of course, bypassing paywalls is ethically questionable and may be illegal in some jurisdictions. That’s why many people choose to do so anonymously on the dark web, rather than using the clear web version of the site.
It works as a decentralized, peer-to-peer network that emphasizes censorship resistance and complete anonymity. In addition to the Tor browser, you should use an antivirus program (like Norton 360) to protect your device from malware infections, and a VPN (like ExpressVPN) to secure your IP address and traffic. Also, only use .onion links from legitimate sources like The Hidden Wiki. However, make sure you’re careful which links you click on — some of them lead to sites that contain illegal content and services. The Dark Web is a complex, multifaceted space, shrouded in secrecy and filled with both intrigue and danger.
Media Outlets With A Secret Door
Simply put, onion sites are websites that are hosted on the Tor darknet that use the “.onion” top-level domain instead of “.com,” or “.gov” for example. All Onion sites use The Onion Router (Tor) protocol to encrypt the user’s connections. It’s only possible to access onion sites through the Tor browser or by setting up some special network configurations. Most internet users love a question and answer forum like Reddit or Quora, on the surface web. The dark web version is Hidden Answers, where users can discuss a wide range of topics anonymously. Just bypass your standard web browsers and fire up your tor browser to get on the dark web to access one of the best tor sites.
What Are Onion Sites?
In 2002 the dark web began to grow significantly when researchers backed by the U.S. The Tor Network provided a way to open safe communication channels for political dissidents, while also offering a channel for American intelligence operatives to communicate from around the globe. Journalists in overly restrictive countries also appreciate the anonymity of the dark web. Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine.
Minimize Or Rescale Your Tor Browsing Window
The three nodes separate your IP address from your destination and enable two individuals to communicate without either party, or any middleman, knowing who the other is. Needless to say, it takes your data much longer to travel this way, which means dark web links load slowly compared to indexed sites. When you try to connect to a .onion website, Tor will route your traffic through three or more randomly chosen nodes before it reaches your destination website. Each server adds a layer of encryption, and this layered system is what lends The Onion Router its name. Ahmia is a dark web search engine designed to index and search tor websites.
- There’s even an option to set a timer on your most sensitive messages so they disappear after a set time period.
- While its .onion address doesn’t make it much easier to maintain an anonymous account, it does make Facebook more accessible in places where it’s censored.
- Feather is a free and open source Monero wallet available on most major computer platforms.
- Doing so will protect you from accidentally accessing illicit content or becoming a victim of malware.
- Equally important is maintaining strong operational security by using trusted Tor browsers, VPNs, dedicated devices, and disabling scripts that could expose identity,” says Currie.
- Because it’s easier to contain malware in a virtual environment, which can be fully controlled.
The service emphasizes privacy with zero-knowledge encryption and no registration requirements. My tests showed reliable performance for smaller files, but larger transfers can be slow due to Tor’s limitations. From Flickr to Facebook posthaste – that would be an accurate description of Dark Lair, an image hosting platform turned social media. Dark Lair allows you to post comments, share music, upload photos, message your dark web ‘friends’, and everything in between.

Everything you do is protected by NordVPN, which is key to accessing the dark web and enjoying it privately. You need a special browser (Tor) and all of these websites are intentionally obscured. So, to clarify again, this tutorial will cover how to access the dark web privately and safely – not the deep web. You can go on the dark web safely, use legal sites, and enjoy the experience without worries. In this tutorial, we’ll explain how to access the dark web in complete privacy and cover a few more important factors to consider before starting.



