
Upon detecting a threat, Scout raises an alert in the monitoring dashboard. It is then up to the network administrator to manually shut down the network traffic or use any protection software. One impressive thing about this tool is that it has over 50 dashboard views that allow security teams to investigate and analyze insights and search the data. The security researchers assess the breach data early in the breach timeline. This allows the end users to validate user identities and reset passwords before the hackers misuse them. Being one of the best dark web monitoring tools, ACID works throughout the year and investigates deeply into the dark web to find any clue of malicious activities targeting the clients.

Why BreachWatch Is The Best Dark Web Monitoring Tool
It stands as one of the most prevalent search engines utilized within the TOR Browser ecosystem. DuckDuckGo presents a straightforward interface reminiscent of Google’s, featuring a search box at the center of the page where users can input their queries to retrieve relevant results. When choosing a Tor search engine, consider your goals and experience level. DuckDuckGo is ideal for newcomers due to its user-friendly design and reliable privacy features, making it a great option for general Tor browsing.
DarkIQ: Dark Web Monitoring Tool
In this article, We will continue with a structure setup consisting of a simple methodology comprised of several steps and tools that you can successfully automate these steps. – Digital Asset Accessing is sold, such as the database, critical servers, and infrastructures provided to sell infrastructure. – Vulnerabilities are where security vulnerabilities in popular software used in many companies are sold.
OWASP TorBot is a web crawling tool with various features designed to explore and collect data from websites on the Tor network, .onion domains, and custom domains. These features, once completed, will provide valuable capabilities for researchers and analysts interested in examining hidden websites and their content. SearchLight is part of the service that provides unparalleled visibility into the organization’s dark web risks. It delivers alerts and can assess an extensive threat intelligence library and historical archive of dark web data for over ten years. In addition, it enables security teams to take immediate action on threats before they cause any damage. The dark web monitoring tool utilizes a combination of automated scanning and human intelligence to scan dark web communities, pages, and sites that are not accessible to ordinary scanners.

With more than 3.8 million newspapers available across 4,300 different titles, there are a total of more than 200 million archives at your disposal. How many times have you come across an academic journal you wanted to read only to find you need a subscription? It has more than 18,000 journals available across 80 languages from 126 different countries. Once you have cloned the repository into somewhere that go can find it you canrun go install github.com/s-rah/onionscan and then run the binary in $GOPATH/bin/onionscan. We test gadgets, dig into tech stories, and tell you what’s actually worth your time and money.
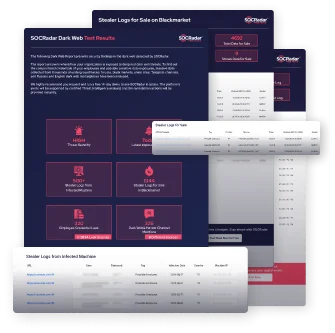
- Understand threats in the top 10 used languages on the dark web – even on posts using dark web Russian slang.
- Identity Guard is owned by Aura and is one of the best identity theft protection solutions on the market today.
- Additionally, if you are on a clear net, a VPN will give you access to blocked websites and content.
- The Invisible Internet Project (I2P) is another dark web browser alternative focusing on end-to-end encrypted private network layers.
- The Kilos search engine is primarily used to find and access dark web markets where illicit drug transactions are one of the main activities.
- These search engines allow users to access onion dark web pages without setting up expermental labs or using specialized equipments.
Mcafee Dark Web Monitoring
All companies need a service like this and the CrowdStrike package is the leading reconnaissance service on this list. As the system includes the input of consultants as well as automated scanners, this is a pricey system. Small businesses on tight budgets should look to one of the other services on this list rather than skipping this category of protection altogether. The Vision system searches for mentions of the client company’s domain and email addresses in hacker data exchanges.
What Is ThreatMon, And How Does ThreatMon Monitor The Dark And Deep Web?
Download AVG Secure VPN to encrypt your internet connection and protect your privacy wherever you go on the web. This process makes tracing the user’s location and activity nearly impossible. The core functionality of the dark web relies on onion routing, a method that encrypts and routes user communications across multiple servers, known as nodes. It has a reputation for being fast and effective, though the content it indexes varies widely in quality and legality.
Legal Risks And Exposure

The oldest dark web search engine, Torch Onion updates its sites every day and has the largest onion search results. It lists results very quickly and its interface is a bit similar to that of a conventional browser. Torch’s wide search capability makes it attractive to people who want to browse the dark web. Ahmia goes beyond being just a search engine; it is used to read statistics, insights, and news related to the Tor network.
Onion City
ATO Prevention is the dark web monitoring tool that safeguards users from account takeover by warning them about compromised passwords before malicious actors can use them. CrowdStrike is a pioneering cybersecurity leader in business for almost a decade. It offers various security solutions but markets its dark web monitoring tool as the CrowdStrike Falcon X Recon. It’s designed to help organizations of all sizes and types detect data leaks and breaches, monitor and track fraudulent activities, and the tools cybercriminal uses. The Invisible Internet Project (I2P) is another dark web browser alternative focusing on end-to-end encrypted private network layers. Unlike Tor’s global network, I2P operates as a more localized, peer-to-peer network.

ACID Intelligence is a leading threat intelligence company that protects companies from cyberattacks on the dark web. It continuously scans and monitors the dark web forums and websites to detect attacks early in the planning stage. After in-depth analysis, it provides real-time information about the potential attacks targeting the organization. It also prepares a response strategy to reduce the consequences and avoid them in the future. It also ensures that businesses never miss out on any critical alert that might put their sensitive data at risk. This allows security experts to involve cybercriminals and negotiate the return of sensitive data, which is rare in other monitoring solutions.
Some VPNs may slow down your connection or conflict with Tor’s routing process. This browser encrypts your connection and routes it through multiple servers, keeping your activity private. Before diving into your research, confirm that the search engine you plan to use supports Tor’s protocols. For example, some platforms may require additional settings or plugins to operate effectively.
Securing Your Privacy And Safety With Dark Web Search Engines
CyberBlindspot is focused on intelligence that directly references your corporate assets. Brandefense can also facilitate takedowns against threat actors should it become necessary, keeping your security posture in a forward lean rather than waiting to respond to active attacks. With an impressive database boasting over 122,811 listings and 7,782 vendors, Kilos provides users with a wealth of options to explore. Its advanced search filters allow users to customize their search criteria, including keyword, price range, preferred cryptocurrencies for payment, and even the type of listing (physical or digital).



