
This early detection allows organizations to identify and respond to threats quickly, reducing the chances of unauthorized access, financial loss, or damage to brand reputation. Organizations need automated dark web monitoring to prevent cyberattacks. In 2022, for example, BidenCash was linked to the breach of over 1.2 million credit card records.
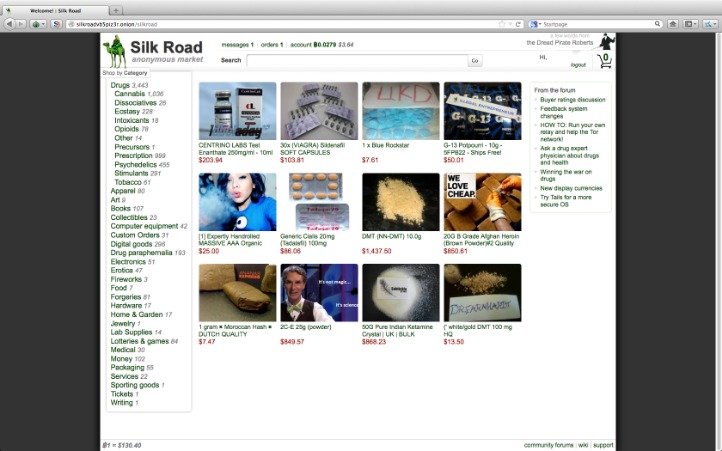
You can find featured listings on the homepage and browse the products of your choice. There’s also a search bar that you can use to search for any particular product or vendor. Bohemia is a modern dark web marketplace with a great user interface that is easy to use and navigate. It asks you to pay the merchant fee if you want to sell something, preventing the buyers from getting scammed.
Introduction To The Tor Network: Security And Privacy
For instance, you can choose the preferred security levels for enhanced protection. The security level is set to ‘Standard’ by default, but you can change it to the ‘safest’ and enjoy more security while accessing the dark web. Having JavaScript enabled on the dark web can cause havoc because it can reveal your IP address to your website. Also, previously, the Tor browser was vulnerable to JavaScript attacks as it provided hackers a pathway to track your activities by using the session details.
Step 1: Use Trusted Dark Web Search Engines
Always use a fake name and a temporary email address when you buy something from the dark net shops. You can even use a secure email provider or a burner email address whenever you visit the dark web. The website has a sleek design and interactive user interface, making it the most preferred choice in terms of user experience. You can pay through Monera and Bitcoin using the escrow system or the traditional market account after making a purchase on this shop. The readers like you support Beencrypted to help keep up the good work. When you purchase using links on our website, we may earn an affiliate commission at no extra cost to you.
E-mail Newsletter

A VPN like Surfshark encrypts your internet connection and makes it harder for others to see your real IP address. This adds another, more reliable security layer to all of your online activity. Insights like these help researchers and advocates understand how and why Tor is being used. With this info, the wider online community can grasp Tor’s impact and its ability to provide secure and anonymous internet access.
Bohemia popped up post-Hydra takedown and brings a fresh vibe—drugs (weed, pills, some coke) and digital goodies like hacked logins, no exact listing count, but it’s growing fast. They take BTC and Monero, and the site’s got a sharp, modern look—vendor profiles are loaded with ratings and reviews, easy to skim. What’s dope is their forums—real talk, not just noise—building trust like Telegram’s side hustle vibe. Escrow’s standard, keeps things fair, and I’ve never seen it glitch out.
This tactic, seen in 2024 with incidents involving Ticketmaster and IntelBroker, could lead to an overall rise in data breaches. Contrary to predictions, the market for cryptocurrency “cleaning” services, or Bitcoin mixers, stagnated. The competitive landscape remained unchanged, with no significant innovations reported. As the world navigated an evolving cybersecurity landscape in 2024, trends in malware, ransomware, and dark web activities highlighted the increasing sophistication of cybercriminal tactics. Tor Links is a backup directory of “.onion” sites in case other directories go offline.
Missing The Wider Landscape Of Digital Harms
Unlike many alternatives that allow user submissions without thorough vetting, we prioritize quality over quantity to maintain a safer browsing experience. Our dedication to transparency and user security makes our directory a superior choice for navigating the dark web in 2025. While the Tor Browser provides strong anonymity, using a VPN (Virtual Private Network) alongside it adds an extra layer of security and privacy. A VPN encrypts your internet traffic before it enters the Tor network, hiding your Tor usage from your internet service provider and shielding your IP address from the first Tor relay.
Facebook Onion Site
Stick to verified dark web directories and legitimate services to minimize your exposure to risks. I always cross-reference links from multiple verified sources before visiting any dark web address. While its name may indicate danger, the dark web can actually be a safe place. It provides safety and anonymity for journalists, privacy-conscious users, or those in high-censorship countries. You need to ensure you’re only accessing reliable dark web sites, and the ones listed below are among the safest ones that currently work.
How Do I Access Onion Sites?
Riseup is available on the surface web, but its presence on the Tor network extends its privacy benefits by letting you use its services without exposing their real-world identities. You can access encrypted email services through the onion site without getting tracked. It’s maintained by a volunteer-run collective from the USA that protects the platform from malicious attacks and pledges to support social justice and progressive causes. Riseup’s secure email and chat help individuals communicate without fear of surveillance or data interception. DuckDuckGo is a reputable US-based software company, so their Tor site itself is safe to use.
By leveraging automated dark web monitoring, organizations can mitigate risks, and take preventive measures before the leaked data is exploited. In addition to its emphasis on stolen credentials, 2easy Market offers a variety of cybercrime tools, such as hacking services, exploit kits, and other resources for conducting cyberattacks. Pastebins are text sharing services, useful for sending and sharing large snippets of code or text.
Multi-vendor Darknet Drug Markets
- The takedown of major groups like LockBit, AlphaBay and Hansa in 2024 demonstrates improved global collaboration among law enforcement agencies.
- Using Tails OS can further security, as all your data is reset every time you close the device.
- This site supports PGP encryption and two-factor authentication features.
- Always withdraw your funds rather than leaving them in a market’s wallet.
- Also, you can set a strong password to protect your message and choose how long it will take to expire.
- Dark web hackers often use malware such as keyloggers, ransomware, and trojan horses to access sensitive information and cause damage.
As a criminal market, it is deeply intertwined with a wide range of criminal activities, including cyber-dependent and financial crimes. As these illicit economies continue to flourish, tackling and dismantling the criminal networks involved will require more than technological advancements. The issue calls for international cooperation, policy adjustments and a deeper understanding of the constantly evolving cyber landscape.
How To Buy Credit Cards On Darknet?
While a threat actor doesn’t generally care about the type or size of the organization they target, their motivation generally, although not always, points to the victim. Understanding these motivations helps to plan effective cybersecurity strategies. Malware is any software that is designed to harm or exploit a computer system. Dark web hackers often use malware such as keyloggers, ransomware, and trojan horses to access sensitive information and cause damage.
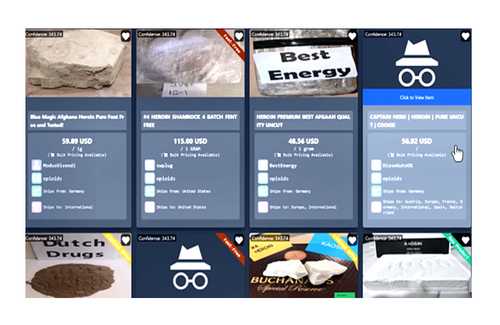
It was touted as a major policing win and was accompanied by a slick cyberpunk-themed video. Whether you’re a business owner or not, you should look to protect yourself from cybercrime on the dark web. Here are some steps you can take to help prevent your personal information from being accessed and shared online. Credential-based attacks are a form of cyber threat where attackers use stolen or forged credentials to gain unauthorized access to systems and data.



