It’s known for its strong security features (like a trusted escrow system, PGP two-factor authentication) and anonymity....
wpadmin
In 2024, we anticipate an expansion in the variety and complexity of these services. This expansion is...
She combines her background in digital marketing from DePaul University with a passion for cybersecurity to create...
Credit monitoring services protect your credit score by notifying you of changes in your credit report and...
The investigation led to Ayres’ home address, and when officers went to his house they uncovered 295...
Vulnerability management (VM) is the proactive, cyclical practice of identifying and fixing security gaps. In October 2023,...
To even gain access to the dark web, all users have to download Tor. One of the...
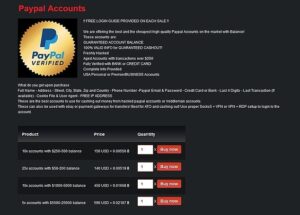
Stolen credit card details are sold for a fraction of their actual value, making it an attractive...
There’s truth to this, but the dark web also offers a welcome refuge from overbearing government surveillance...
The middle node knows the previous node but not your IP address or what you’ve requested online....