Many experts advise against using third-party mobile browsers that utilize the Tor Network. No standard web browsers can be used to access dark web content. The easiest way to access Tor is through a special browser known as the Tor Browser.
The 9 Most Private Cryptocurrencies In 2025

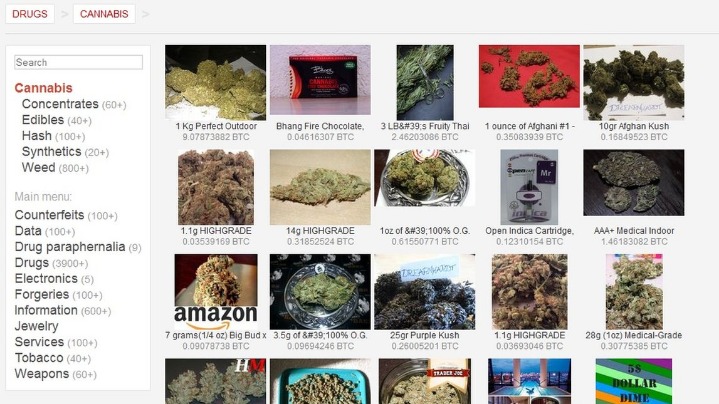
Darknet Markets are online marketplaces where people can buy and sell illicit goods and services under the protection of the anonymity by TOR. The products that are most commonly listed for sale include drugs, fake documents, fraud-related items, and hacking services and tools. You can access the black market by navigating to the right “.onion” addresses. These sites are typically not listed on Google or other search engines. You can find them on private forums, message boards, and communities that work only by invitation. This is also a slippery road because many marketplaces get taken down by law enforcement or replaced by scam sites that can lead to malware or data leakage.
Cybercrime Increasingly Moving Beyond Financial Gains
Learn effective strategies for conducting threat hunting in your organization. Singularity™ Threat Intelligence provides insights into adversary tactics and helps mitigate these risks before they impact your organization. Abacus Market is a conceptual platform to illustrate privacy and security best practices.
However, Monero, on the other hand, is untraceable and the most trusted payment method on these markets. Therefore, most cybersecurity experts recommend using Monero while shopping on darknet markets. The anonymity and lack of rules that define darknet marketplaces are exactly what make them breeding grounds for fraudulent activities.
- The connection is encrypted, and all the traffic bounces between relays worldwide, making the user anonymous.
- The advantages of I2P are based on a much faster and more reliable network.
- Second, shutting down or controlling access to the dark web would be a huge undertaking and could have unintended consequences.
- STYX MarketSTYX Market, launched in 2023, is all about financial crime.
- Here is what newcomers like me need to know before attempting to access these dark web markets.
This is to address security concerns and to improve its presence. Today, Exodus Marketplace works from 3 different domains, two of which are its mirrors. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. However, it has a sneak peek, easy guide steps, and/or a quick list providing quick in-page navigations and easily-found answers if desired. As I’ve previously said, it’s a good idea to keep your interactions with the dark web to a minimum, unless you can absolutely trust the people you’re dealing with. You’ll often see a sign in stores that says “look, don’t touch,” and it’s not a bad adage to bear in mind as you navigate around the dark web.
Table Of Contents
Unlike surface web platforms, darknet markets have no reliable way to verify vendors. Many “trusted” sellers use fake reviews or steal reputations from shutdown markets. Stay informed about the latest darknet marketplaces, secure browsing practices, and privacy tools. That doesn’t mean it’s impossible to track users on the dark web. If you log into personal accounts on the dark web or visit websites with tracking scripts, then your activity may be tracked.
WeTheNorth is a Canadian market established in 2021 that also serves international users. It offers counterfeit documents, financial fraud tools, hacking and malware services. It has an active forum and community along with an extensive user vetting process. Launched in 2023, STYX focuses on financial crime, providing stolen credit card data, hacked bank accounts and access to various cryptocurrency laundering tools.

Darknet Markets Explained: Navigating The Hidden Web
If you ever decide to explore the dark web, protecting your identity is crucial. Most people start by using the Tor Browser, which hides your IP address. Some markets are invite-only or have strict registration rules to keep out scammers and law enforcement. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down.
- Transactions within dark markets predominantly involve cryptocurrencies like Bitcoin, Monero, or Ethereum.
- Legally, they are limited to observing publicly accessible areas using tools like the Tor browser, without engaging in unauthorized access or illegal transactions.
- Yes, it often deals with illegal content for illicit purposes in a hidden part of the web called dark web.
- However, the website has some security risks, and users experience glitches.
- It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security.
- Accessing darknet requires using Tor Browser, a special web browser that routes your internet traffic through a global network of relays managed by volunteers.
How To Access And Trade On Darknet Markets

The advantages of I2P are based on a much faster and more reliable network. Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains. I2P can only be used to access hidden sites that are only available on the I2P network.
Transactions Completed
The most common darknet software is the free and open-source Tor, short for the Onion Router. The software was developed in the mid-1990s to protect U.S. intelligence communications online and is used in conjunction with virtual private networks (VPNs). While some competing darknet softwares are similar to Tor browsers, they typically exist for different purposes. For example, the network dn42 exists to help users form connections and networks rather than to preserve user anonymity. The difference between the dark web and the deep web is that the deep web refers to websites and web pages that aren’t indexed by search engines, like login pages and payment portals.

The “VPN-over-Tor” approach offers added protection, even if Tor is compromised. By encrypting communication before it gets to the Tor network, pairing Tor with a VPN gives a second degree of protection. By distributing communication over several nodes, it obscures the user’s IP address.
Exploitation Of Anonymity For Harm
Tor works by encrypting traffic and bouncing it through a distributed network of relays run by volunteers all around the world, protecting users’ anonymity. This makes it much more difficult to trace internet activity, revealing where users visit or what they do online. However, accessing these markets carries legal and safety risks given the lack of oversight and abundance of scams.
Even after Silk Road went down, dark web marketplaces haven’t slowed down. Stopping their growth takes serious effort from US agencies like the FBI, often working hand-in-hand with international law enforcement. They sell these files for just a fraction of the original cost on the surface web or even share freely, which makes them tempting for people looking for shortcuts.
#1 Install A VPN

However, having a faster computer does help as you’d be running Tor + the VPN. I’m sure you’ve learnt how to access darknet markets by now, haven’t you? Before I wrap this up, let me answer a few basic, most frequent questions around the topic. Bottomline, you’re bound to find links to darknet markets here. It’s a myth that you must be a tech-whiz in order to access darknet markets as shown in movies.
This way, it becomes very difficult to trace which websites you’re visiting, and these sites won’t know where you are located. Once you have found a darknet market URL, you will need to create a Tor account in order to access the market. This process is similar to creating an account on any other website, but with a few key differences. For example, you will need to use a pseudonym and a secure password, and you should avoid using any personal information that could be used to identify you.



