
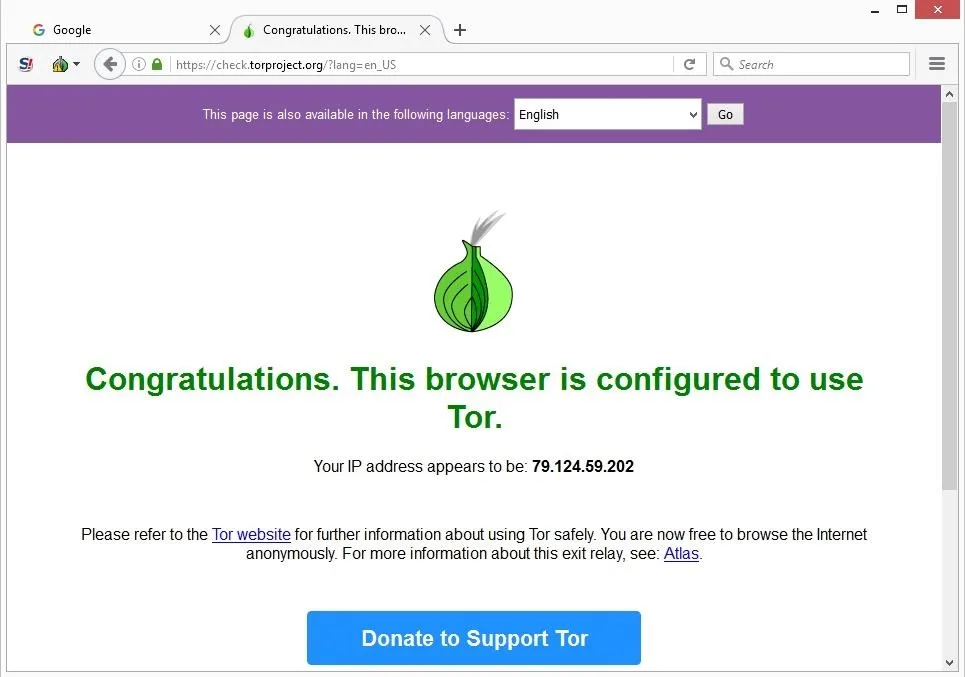
In a nutshell, the deep web includes anything behind login walls, while the dark web is a small, deliberately hidden portion of it. Examples of the deep web include your personal banking login portal and academic databses. Visiting a dark web site requires specialized software like the Tor Browser, which routes traffic through a series of random relays across the globe to mask both origin and destination. No matter what you do online, there’s always at least some risk of being tracked — especially on the dark web.
Malware And Phishing
Tor routes data through at least three servers, and websites will only see the IP address of the last server, not yours. It has features to maximize your privacy, unlike standard web browsers that have less stringent privacy protections. However, using Tor has some challenges that you should be prepared for. Darknet marketplaces can be surprisingly similar to sites you find on the surface web—complete with limited-time sales, customer reviews and advertisements for organic products. However, criminals use these marketplaces to sell illegal products and services, including drugs, weapons and hacking software.
Best Dark Web Sites: Unseen Onion And Tor Links
By disabling, you reduce such attacks’ potential (especially on untrusted websites). As such, you should exercise caution when accessing any unofficial dark websites. Alternatively, users can connect in opennet mode, which automatically assigns peers on the network.
Legitimate Use Cases For The Average User

Operation Onymous in November 2014 seized roughly 400 Tor sites and arrested 17 suspects, including operators of Silk Road 2.0. Six years later, Operation DisrupTor targeted opioid traffickers, netting 179 arrests and $6.5 million in cash and crypto, while removing hundreds of kilos of narcotics from circulation. Each wave of takedowns disrupted marketplaces but also pushed criminals toward more resilient, decentralized models. In February 2011, Ross Ulbricht—using the alias “Dread Pirate Roberts”—opened Silk Road, the first modern darknet marketplace.
What Is The Dark Web? How To Access It And What You’ll Find
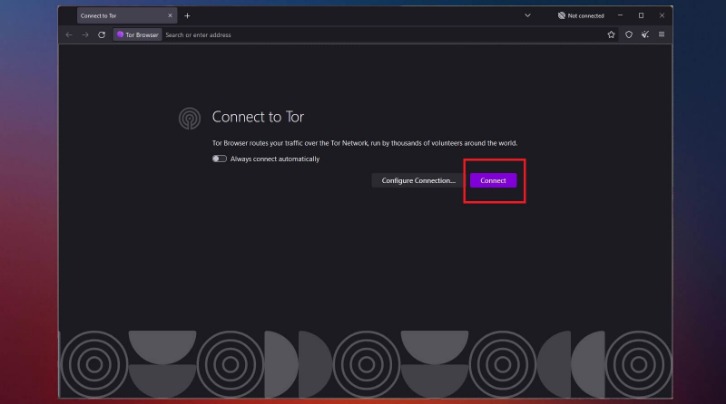
The Tor network combined with a VPN is one of the safest ways to get on the dark web. Many internet service providers (ISPs) and governments are suspicious of Tor use, but a VPN will hide your internet activity and help prevent anyone from knowing that you’re using Tor. The Tor browser is designed to provide improved online anonymity and security. However, be careful when using the Tor Browser to access the dark web. The dark web is a dangerous place, and all bets are off on your safety. This is why I strongly advise anyone visiting the dark web to exercise the greatest of caution during their dark online travels.
You should never trust websites and forums on the dark web with your personal information. You can check our guide on the best VPN services to find the right VPN solution to protect your privacy. These tactics trick users into revealing sensitive information or paying for non-existent products. Like Freenet, I2P has its own dark web that consists of websites ending in b32.i2p. For instance, your email inbox, online banking account, or a company’s internal database resides in the deep web.
While many visitors manage to browse hidden services without incident, staying safe requires constant vigilance. This section outlines the primary dangers and offers practical advice to help you navigate these shadows responsibly. With rising curiosity around hidden corners of the internet, many professionals wonder, “how to access the dark web” safely. From cybersecurity researchers to IT managers, understanding how to navigate the dark web can help monitor cyber threats, protect sensitive data, and investigate cybersecurity incidents. Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for.
Major Risks And Downsides
Connections made while a VPN is active will also be encrypted, helping you stay protected from eavesdropping and man-in-the-middle attacks. You can usually select the location you want to appear to originate from and VPNs will use a collection of servers and relays to make tracing your IP difficult. As search engine crawlers do not catalog these pages, you would need to know the exact link to access a website in this area of the internet. This could include government services to access your records, health care services, members-only areas, intranets, or corporate resources.
While Tor is the most common method for accessing the dark web, I2P and Hyphanet offer alternative options for secure and private browsing. Let’s go through the setup process for each, as well as how to use them effectively. In this setup, the VPN connection acts as a middle layer between your device and Tor, routing your internet traffic through the VPN before it reaches the Tor network. Among the many benefits of using a VPN vs a proxy or Tor is that it provides full encryption for all the data you send and receive online. So not only is your web activity hidden, but you can mask your IP address by connecting via a wide range of global VPN server locations.
Hideme – Best Free VPN For Stealthy Dark Web Access
- Unlike traditional browsers, this will route your internet traffic through an anonymizing network and mask your IP address.
- The dark web is simply a part of the internet that requires special tools like the Onion Browser to get access.
- Using the ProtonMail .onion site offers security and privacy advantages.
- This involves passing internet traffic through the Tor network first, and then through the VPN.
In short, even with Tor, there’s no perfect anonymity online, but there are efforts to claw back our power online, says Lewis. There are other ways for spies, hackers or other adversaries to target Tor. Lewis points to the “first contact problem”, when an attacker spots when someone moves from non-private tools to private ones, noting it’s been used to identify whistleblowers. What should you do if your information is found in a data breach or you think it’s been leaked somewhere? Change your passwords and watch out for suspicious activity on your credit reports.
- To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web.
- Tor provides users with a higher level of privacy, which is particularly attractive to threat actors, cybercriminals, hackers, and government operatives who want to keep their identities secret.
- Unlike the publicly accessible surface web, the deep web includes sites requiring login credentials but is still accessible via traditional browsers.
- The connection is encrypted, and all the traffic bounces between relays worldwide, making the user anonymous.
- NinthDecimal is the leading media and technology service provider for the WiFi industry.
Outside of work, she is a travel enthusiast, music lover and avid learner interested in global cultures, spirituality, psychology and neuroscience. Stay informed about the latest darknet marketplaces, secure browsing practices, and privacy tools. More seriously, free VPNs – particularly those offered as standalone services – sometimes make money by selling your data to third parties. These aren’t the type of products you should use to keep you safe while exploring the dark web.

We’ll focus on secure, ethical practices tailored to cybersecurity professionals and IT leaders. Sections of the dark web are often closed down too, as part of police operations. Bear in mind too, that your internet provider will be able to see you connecting to Tor nodes, even if it doesn’t know exactly what you’re doing.
There are both free and paid VPN services, but if you’re planning on accessing the dark web, you’re going to want to opt for a high-quality paid VPN that offers you plenty of protection. A VPN encrypts your internet connection and masks your IP address, making it difficult for anyone to trace your online activities back to you. Finding content on the dark web isn’t as straightforward as using Google. You’ll need a specialized dark web search engine, like Ahmia or DuckDuckGo’s Tor service, which can help you locate onion sites (also called Tor sites).
You may already be aware that malicious actors can use these to harm your credit, engage in financial theft, and breach of your other online accounts. Leaks of personal data can also lead to damage to your reputation via social fraud. Yes, simply accessing the dark web is legal in the United States. Downloading Tor or browsing .onion sites doesn’t break any laws on its own. Journalists, whistleblowers, and researchers often use it to protect their privacy or gather sensitive information. Like the regular surface web, the dark web offers its own social media sites and web forums.
Tor Browser is available for multiple operating systems, including Windows, macOS, Linux, and Android. It is free to download and use, with the goal of promoting online privacy and freedom of expression. That said, anonymity comes with a dark side since criminals and malicious hackers also prefer to operate in the shadows. For example, cyberattacks and trafficking are activities that the participants know will be incriminating.



