
But again, your ISP won’t be able to see any of the content you’re reading or what you are sending and receiving through the Tor network. It has been estimated that a large percentage of dark web traffic is related to illegal pornography that includes underage victims. Business operational data, such as operational data, financial data, intellectual property, and trade secrets can be found on the dark web. There are a number of services and tools available on the dark web, many of which can be used for nefarious purposes. As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously.
Stolen Data And Identity Theft
The buyers, or “consumers,” are cybercriminals who use these tools to launch illegal activities. The victims, who are common users, businesses, and even banks, who end up paying the price. As we mentioned earlier, not everything sold on dark web markets is illegal. As terrible as its reputation may be, some vendors sell legitimate goods or services. Some customers even use the dark web to make anonymous purchases, especially in areas where privacy is a huge concern. BidenCash was launched in 2022, and since it became a hot spot for cybercriminals to sell and buy illegal things, including stolen card information and personal data.
Its commitment to privacy, diverse product offerings, and robust security measures make it a preferred choice for users seeking discreet transactions within the darknet. Some are looking for illegal stuff they can’t buy elsewhere, like drugs or counterfeit documents. Onion sites can be safe in terms of privacy protection due to strong encryption, but they also host a significant amount of illegal content and scams.
Silk Road Dark Web: History And How It Shaped Online Crime
- As one marketplace is taken down, another often rises in its place.
- Each time there’s a system update offered to you, download and install it, as such patches reduce the chance of your data being compromised.
- These markets are dangerous anyway and shouldn’t be accessed even if they’ve onion addresses.
- So, you can come across images, photos, videos, or chatrooms with extreme violence, exploitation, or other disturbing stuff.
- Great life advice, but it’s even more valuable where the darknet is concerned.
Later in 2022, the US Naval Research Laboratory built on Freenet’s idea to create a secure and encrypted network for sensitive communications, which was later released to the public as open-source software. If you take a quick look through darknet marketplaces, you’ll instantly notice an overwhelming supply of pirated content. We’re talking about even early access to unreleased music, leaked TV episodes, concert footage, and even popular video games before they officially drop. But somewhere between production and purchasing, things can get dirty.
A Brief Overview & History Of Darknets & Dark Markets

Cybercriminals can rent or buy malware tools through darknet markets. This malware-as-a-service model allows less tech-savvy criminals to launch malware-driven cyberattacks without building the tools themselves. One of the most common types of illicit goods is stolen login credentials, often collected from data breaches. These “credential dumps” allow criminals to access online accounts, steal identities, and commit fraud. Law enforcement agencies monitor many dangerous markets, and even anonymous browsing isn’t foolproof. Just visiting these sites can attract attention from law enforcement, especially if you interact with known vendors or download suspicious content.
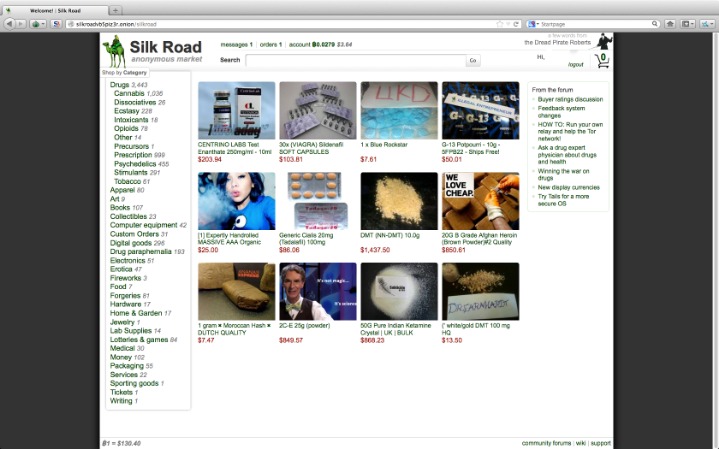
What To Do If You See Something Illegal
You should only ever access websites you know are safe because they’re vetted by websites or other sources that you already know are safe. Take a look at the sites that these directories have collected and see what topics interest you. If you want to improve your security further, you could also use a VPN at the same time as Tor. For the most security-conscious, you can even install the Tails operating system on a flash drive and run Tor from that.
Best Dark Web Sites: Unseen Onion And Tor Links
In some countries, such as China and North Korea, the government uses heavy online censorship and blocks many dark web websites. This is where an Onion website, like the Tor browser, comes in handy. The social media giant is also aware of the many attempts by repressive regimes to restrict its access. After all, it enables users to connect and communicate with each other from around the world. You can choose the best darknet (.onion) website that suits you and start surfing.
- It recovered, but then when China banned their financial institutions from interacting with Bitcoins, the value dropped over 50%, by more than $500 USD.
- It is a specific Debian-based version of Linux software that leaves no traces of the user activity or the operating system on the computer.
- Therefore, most cybersecurity experts recommend using Monero while shopping on darknet markets.
- As these marketplaces keep changing, it is critical to stay on top of the main platforms on the dark web worth monitoring.
- Users leverage these platforms to organize protests, whistleblow, share survival guides, or share files P2P.
The DarkExchange Platform
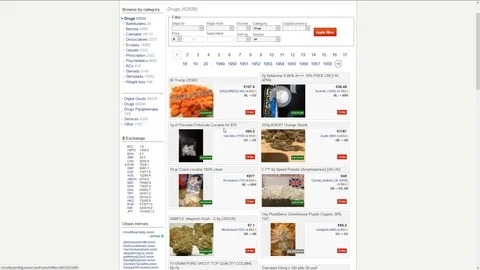
As cyber attacks accelerate and nefarious actors all over the globe seek to more rapidly connect with buyers of illegal goods and information, the term Dark Web has entered the lexicon in a prominent way. Exploring the dark web can be eye-opening, but it’s also risky without the right protection. While the Tor browser boosts privacy, pairing it with a VPN adds a critical layer of security. On the dark web, traffic is routed through multiple server nodes that don’t log activity, obscuring the user’s origin and enabling anonymous communication.
A 2014 study found that the most common type of content found on Tor, the most popular darknet, was child sexual abuse material. The dark web also helps individuals communicate about or sell illegal items such as weapons, drugs, malware, etc. Many people see hacked information and stolen card data being sold on the dark web. For example, you can find information unavailable to the public and share data privately while protecting your online identity.
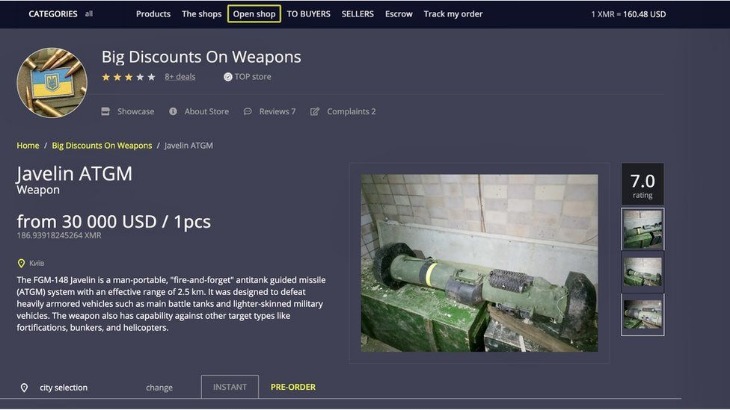
Due to the privacy-forward ethos of the Tor project, Tor Metrics stresses that the data it collects must not undermine the anonymity or security of the network. The best dark web websites provide access to educational materials, host secure services, or bypass censorship. Dark web websites are hidden under layers of encryption that cloak user activity, which can be a boon to whistleblowers, activists, and others who don’t want anyone tracking their activity. The black market, also known as the shadow economy or the underground economy, is a market where illegal goods and services are traded. This can include anything from drugs and weapons to counterfeit goods and stolen property. Aleksandar Kochovski is an expert in cybersecurity with a pronounced emphasis on secure cloud storage, a key component of modern cloud computing.
Security Bundle
The user’s location and the usage are hidden from anyone conducting network surveillance or traffic analysis. Most of these free software options make it more difficult for Internet activity to be traced back to the user, including website visits, online posts, instant messages, and other communication forms. Overall, dark-web marketplaces inherently involve substantial risk, and users must thoroughly understand these threats. Anyone considering engaging with these platforms must carefully evaluate potential consequences, exercise stringent security practices, and remain vigilant to minimize exposure to these significant hazards.
The US Naval Research Laboratory developed The Onion Routing (Tor) project in the late 90s. A network browser gives you access to sites with the ‘.onion’ registry operator. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship. The Dark Web is the part of the deep web that is not indexed by search engines, like Google or Bing.



