
Since Hidden Wiki maintains all kinds of websites, ensure you don’t open something you don’t want to see. It is an excellent option if you want to surf the web anonymously. Even without monitoring your browsing activities, DuckDuckGo will offer decent answers to your questions. Purchases through links on our pages may yield affiliate revenue for us.
- Accidental leaks at the Tor entry nodes can potentially expose your IP address.
- ActiveX and Java frameworks are susceptible to being exploited by hackers.
- And then there’s malware—click the wrong link or download the wrong file, and your device could get infected.
- The dark web, on the other hand, is a small part of the deep web that requires special tools like the Tor browser to access.
- (Some people also seek fentanyl and there are vendors who openly sell it.) Still, my sources agree, unwanted fentanyl is found in lower levels in drugs bought online compared with street drugs.
- Brian, a writer, harm reduction supporter and avid drug consumer in his 60s, hasn’t ever bought directly from the dark web.
Does The CIA Have An Onion Site?
If you choose to visit the dark web, you must take the necessary measures to protect your privacy and security. This includes using an anonymous browser like Tor, a VPN to encrypt your connection, an antivirus for protection against malware (we recommend TotalAV), and generally being careful not to reveal personal information. Being able to order drugs for self-medication so easily and discreetly, Marie continued, also kept misguided friends from trying to force her to quit.
Newsletters
As AI becomes more accessible, hackers may use AI-driven tools to automate data theft on a massive scale. The dark web is a portion of the Internet that is inaccessible to normal search engines. North America, Northern Europe and Western Europe are also major consumer hubs. According to the latest Index, North America’s average drug trade score rose by 0.13 points, while the scores for Northern Europe and Western Europe increased by 0.31 and 0.27, respectively.
Using Onion Over VPN — All You Need To Know

In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web. You should stay away from everything labeled “porn”, “card skimming services”, “PayPal hacks”, “firearms”, “real fake IDs and passports”. Believe me – there are plenty to go around and each and every one of them are being kept under surveillance. Not to mention the fact that you’ll get exposed to some stuff that will definitely make you take several cold showers. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen. Well, now it’s time to fire up Tails and do a little bit of tinkering.
Enjoy More Secure Browsing With A VPN

Notably, the 2023 Index also reveals a ‘strong and statistically significant’ correlation between the synthetic drugs trade and cyber-dependent crimes. According to the Index, the online purchasing of synthetic drugs may suggest the existence of an established cyber environment, which implies a heightened risk of cyber-dependent criminality. The best dark web websites provide access to educational materials, host secure services, or bypass censorship. Dark web websites are hidden under layers of encryption that cloak user activity, which can be a boon to whistleblowers, activists, and others who don’t want anyone tracking their activity. You can tell you’re on the dark web if you’re accessing websites with .onion addresses on the Tor Browser or a similar anonymity network.
While no approach is foolproof, a thoughtful, criteria-driven strategy ensures a more secure and beneficial experience on the dark web. The Internet is a vast and complex landscape, much larger than the familiar interface we use every day. If you have a good story idea or tip, you can reach him by email at or on Twitter @ReidSouthwick. Another 24 per cent of sellers didn’t indicate the country they were shipping from. The United States topped the list, with a quarter of vendors shipping from south of the border, followed by the United Kingdom, at nine per cent. “To me, that’s very different than buying books or other things from people on a used market, where the risk is you don’t get that product, versus this product could potentially kill you.”
- It also boasts that no personal information is required to use the service, and payment can be made with cryptocurrency.
- As a result, you should avoid opening unfiltered sources, torrent sites, and dark web links unnecessarily and downloading every file you come across.
- The “surface web,” on the other hand, is the publicly available part of the internet that search engines index.
- Tor has around 2 million daily users exploring over 65,000 onion sites.
- In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web.
- Riseup is a volunteer-run social movement organization that offers email, email lists, a VPN, online chat, and other online services for political activists engaged in various causes.
Digital Libraries And Academic Archives
If you need a great Tor VPN, I recommend ExpressVPN — all its servers allow Tor traffic, it has excellent security and privacy features, and it provides fast browsing speeds. SecureDrop protects your privacy by encrypting your data, which makes it unreadable. Also, it doesn’t log your IP address or any information about your browser or device. Moreoever, the servers are owned by the organizations that use the service. I tested the dark web version of Facebook and it worked very well — I successfully logged into my account (I only had to verify my identity via an email message), browsed my news feed, and chatted with my friends.
Ransomware gangs are also expected to diversify their tactics, targeting smaller companies and individual users to maximize their reach. Businesses should prepare for more sophisticated ransomware campaigns, potentially leveraging AI to exploit security gaps. The takedown of major groups like LockBit, AlphaBay and Hansa in 2024 demonstrates improved global collaboration among law enforcement agencies. However, this will likely lead to the rise of new, decentralized groups like RansomHub. State-sponsored threat actors are cybercriminal groups supported or directly managed by government agencies on the darkweb market. They often carry out attacks that align with their country’s political, economic, or military goals.

The Birth And Rise Of The Silk Road
One of its best features is Anonymous View, which is a free proxy that masks your identity while you’re browsing sites. It also always uses a secure HTTPS connection, so you’re safer on public Wi-Fi networks too. DuckDuckGo also lets you access chatbots anonymously, has image, video, news, shopping, and other search options. Another cool features it you can sort results by age (past day, week, month, or year), and lots more. Plus, it lets you set your location for local results, manage safe search filtering, and there’s even an AI “Assist” tool that provides AI search results — so you don’t have to visit web pages to find your answer. So, I put together a list of the best dark web sites in 2025 to help you get started.
The operation resulted in the seizure of 50.8 million euros ($53.4 million) — in cash and virtual currencies, nearly 1,900 pounds of drugs and 117 firearms in a series of raids in several countries. The agency, based in The Hague, built intelligence based on evidence from Germany, which it said seized the marketplace’s “criminal infrastructure” in December 2021. SecureDrop is one of the most reliable file-sharing sites on the deep web. SecureDrop helps whistleblowers anonymously send sensitive material to media outlets via a unique SecureDrop URL. The files are automatically encrypted, and the sender’s IP is not logged.

Riseup is available on the surface web, but its presence on the Tor network extends its privacy benefits by letting you use its services without exposing their real-world identities. You can access encrypted email services through the onion site without getting tracked. You can access DuckDuckGo on the surface web, but a Tor version is also available. You’ll get unbiased, organic search results without getting any of your browsing behavior logged. Using DuckDuckGo over Tor will also let you see onion sites and normal pages in your search results.
The Shift Toward Smaller, More Niche Markets
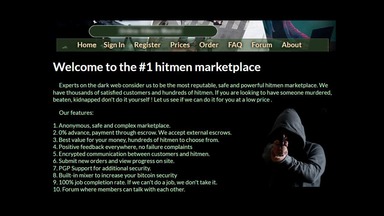
By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet. Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data. The Tor browser, short for The Onion Router, is software that allows users to access the Tor network. Navy, it anonymizes Internet activity by routing data through multiple servers, masking your IP address. Despite the attempts to secure the Silk Road’s activities, the platform caught the attention of law enforcement. In 2013, the FBI successfully traced Ulbricht and seized the Silk Road.
Haystak also offers a premium version that allows advanced search, access to historical content, and email alerts. The three nodes separate your IP address from your destination and enable two individuals to communicate without either party, or any middleman, knowing who the other is. Needless to say, it takes your data much longer to travel this way, which means dark web links load slowly compared to indexed sites. Encryption technologies allow vendors to communicate with customers and receive payments anonymously.
This .onion link makes it impossible for hackers to impersonate your profile. It has a feature called CoinJoin that combines multiple coins from different users into a single transaction. This makes it extremely difficult to find out who you are transacting with. The good news is that the platform will not see what you copy/paste. Your data is encrypted in the Tor browser before reaching the ZeroBin servers. ZeroBin is a wonderful way to share the content you get from dark web resources.



