
Still, the existence of this content is a grim reminder of the dark web’s potential for abuse when left unchecked. In many countries, strict laws limit who can legally buy, own, or carry firearms. Notably, Abacus explicitly forbids highly dangerous goods, including weapons, explosives, and exploitative material, which has helped maintain a relatively favorable reputation among its user base. They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails. Cybersecurity experts should pay close attention to these trends, as they often indicate emerging threats and profit-generating tactics among the cybercriminal forums. Never log in with your real name or reuse passwords from other accounts.
Abacus Market (Best For Cryptocurrency Transactions)
The market is especially well-known for providing access to freshly compromised data, often obtained from recent breaches and stealer logs. One of the distinguishing features of Fresh Tools Market is its focus on providing up-to-date, freshly obtained tools and credentials. He recommends verifying market employees carefully, and to weed out law enforcement infiltration through barium meal tests. The reputational damage inflicted by a breach can be just as devastating.
What Is The Difference Between The Deep Web And The Dark Web?
Launched after the takedown of AlphaBay in 2021, Abacus Market has rapidly risen to prominence. It features over 40,000 listings including narcotics, counterfeit items, hacking tools, and stolen data. The marketplace is well-known for its bug bounty programs and robust security mechanisms, including mandatory 2FA. Organizations should conduct regular cybersecurity awareness training that includes mobile security and phishing simulation tests. Also, criminals are increasingly using databases of stolen employee mobile phone numbers to attack employer networks.

Latest News
Our regional data reveals that most people buying stolen credit card data on UNICC are from North America (after Global), while most of those selling it are from China. While it’s difficult to say exactly why that is, it’s possible that more criminals from China have the technological proficiency to steal credit card data. The goods and services on offer range from leaked credit card details, exploit kits and hackers for hire, to advertisements for hitmen services. You can buy credit card numbers, all manner of drugs, guns, counterfeit money, stolen subscription credentials, hacked Netflix accounts and software that helps you break into other people’s computers. Buy login credentials to a $50,000 Bank of America account, counterfeit $20 bills, prepaid debit cards, or a “lifetime” Netflix premium account. The migration of vendors, plus the timing and source of OMG’s initial revenue suggests that Hydra administrators may have been involved with the development of OMG.
Businesses face substantial cybersecurity risks due to the proliferation of these marketplaces. Data breaches often lead to sensitive corporate information appearing on the dark web, which can fuel further attacks. A security gap analysis can help businesses identify vulnerabilities that hackers exploit to compromise their data. Additionally, investing in cybersecurity services for small businesses ensures stronger defenses against threats originating from these illicit platforms. Notable dark web marketplaces, such as the infamous Silk Road, revolutionized this underground economy by introducing a centralized platform for illicit trade. Silk Road, operational from 2011 until its shutdown by the FBI in 2013, demonstrated the scale of these marketplaces, with thousands of users worldwide.
- Link lists like The Hidden Wiki are another option, but even indices also return a frustrating number of timed-out connections and 404 errors.
- Besides this, it supports wallet-less transactions and accepts payments through Bitcoins, Litecoin, Monero, and Zcash.
- The more proactive you are, the better you can protect yourself against identity theft and other cyber threats.
- Abacus Shop is a conceptual darknet market used to illustrate privacy, security, and decentralized commerce.
- The Silk Road was a famous dark web marketplace where users could buy and sell goods and services anonymously.
- This is where an Onion website, like the Tor browser, comes in handy.
Primary Risks And Dangers Of Using Dark-Web Marketplaces
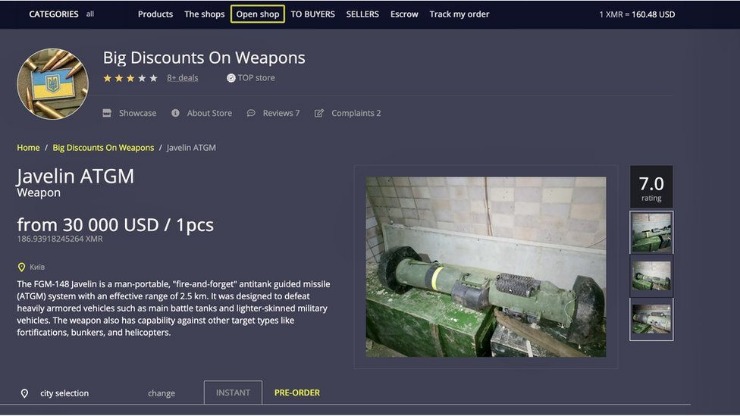
These markets mimic traditional e-commerce websites, but instead of second-hand books or vintage jackets, they traffic in illegal goods and criminal services. The Silk Road was a famous dark web marketplace where users could buy and sell goods and services anonymously. All the payments were made through cryptocurrency, further enhancing marketplace anonymity. The users on this site can review and rate the products that promote reliable and fraudster vendors. Using a reliable VPN provider helps keep you safe when you access marketplaces on the dark web. A VPN encrypts the data traffic and keeps your activities private on the dark web.
In many places, including the U.S., the UK, and the EU, accessing the dark web is legal for legitimate purposes. However, many sites on the dark web host illegal content or activities, and engaging with those can lead to serious legal consequences. In some countries, like Russia or China, dark web access itself may be blocked or penalized. Riseup is a volunteer-run collective that offers secure chat and email services primarily used by progressive activists and social justice communities.
History Of Dark Web Marketplaces
Whereas the deep web is the part of the web not searchable by traditional search engines and requires special tools to access it. Also, you must log in or have a specific IP address or URL to access the deep web content. The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome.
Frequently Asked Questions (FAQs) About Dark Web Marketplaces
It doesn’t use JavaScript, meaning the website won’t track your activities or exploit vulnerabilities. The website allows a personalized searching experience, where you can search according to your geographical location, country-specific, and keyword or price-specific search results. Since the dark web can be accessed through the Tor browser, use a VPN with the Tor browser to ensure increased protection. A VPN hides the fact that you’re using Tor, which is blocked in some countries and always raises doubts because of its criminal reputation. One of the biggest problems cybersecurity teams face isn’t a lack of tools — it’s too many alerts. While this topic may seem distant for most people, understanding how these spaces operate is crucial.
Why Is It Critical To Monitor Dark Web Marketplaces?
By using Forest VPN, you ensure that your internet service provider (ISP) and other potential eavesdroppers cannot trace your online activity back to you. Having JavaScript enabled on the dark web can cause havoc because it can reveal your IP address to your website. Also, previously, the Tor browser was vulnerable to JavaScript attacks as it provided hackers a pathway to track your activities by using the session details. Therefore, for security reasons, disable JavaScript on the Tor browser and enjoy an anonymous browsing experience on the dark net. The website allows visitors to view all the goods and services on display before they buy something.

Helping in the operation were law enforcement authorities from the U.S., Switzerland, Moldova and Ukraine. Law enforcement officials are getting better at finding and prosecuting owners of sites that sell illicit goods and services. In the summer of 2017, a team of cyber cops from three countries successfully shut down AlphaBay, the dark web’s largest source of contraband, sending shudders throughout the network. The market frequently makes headlines for releasing massive troves of stolen data, often as a way to advertise its services. The Russian Market has been around since 2019 and is one of the more prominent dark web marketplaces. Unlike many other dark web markets, Cypher does not require buyers to deposit cryptocurrency upfront, which reduces the risk of exit scams.


While not an onion site, Tor Metrics can provide a fascinating peek “under the hood” of the dark web. It tracks Tor user activity by region, showing trends in access and adoption without collecting personal data. These insights help researchers and privacy advocates understand where Tor is most relied upon, often highlighting global patterns in censorship, surveillance, and the demand for online anonymity. Facebook’s onion mirror allows people to access it in countries that block the platform, allowing people to connect across digital borders. That said, the social network’s data collection and tracking practices may seem at odds with many of the principles motivating dark web users.



