Also contained within it are forums for discussion that include everything from hacking services to human trafficking. The deep web and dark web have many uses, but they also come with risks. If you know anything about data privacy and protecting yourself from identity theft, it’s easy to mitigate these risks on the deep web.
- It could be argued that the dark web could not exist in its present form without the anonymity that digital currencies provide.
- There isn’t any one way to access the deep web — it just depends on what you’re looking for.
- The dark net, found on the net where search engines fear to tread, operates on the principle of onion routing.
- The single-largest chunk of the Deep Web actually consists of statistics and databases, with U.S.
Internet users familiar with encryption and cybersecurity likely know about VPNs, which can also mask your IP, but only to a certain point. Meta (Facebook’s parent) made this onion website for its users on Tor browsers because it showed errors for its normal website (facebook.com). Therefore, it’s a perfectly safe place on the dark web, like many other onion sites you can easily google.
The US Department of Defense developed Tor, which is now run as a nonprofit by volunteers. It is funded by the likes of the US government and the National Science Foundation. The dark web isn’t all illicit deals and seedy undertakings; it’s used for an array of purposes. Internal documents from the deep web leak onto a dark web marketplace. Monitoring by SAGA® identifies the exposure, enabling a swift legal and technical response. Regulations like GDPR, HIPAA, and company policies treat deep web and dark web data differently.
Expert guidance and strategic advice to address unique cybersecurity challenges. Advanced log management and security information and event management (SIEM) solutions for proactive threat detection and response. It comprises just a tiny fraction of the Deep Web, but its potential for misuse makes it a subject of significant concern for security teams and law enforcement. As a subset of the Deep Web, the Dark Web represents an even smaller, more specialized portion of the online landscape. Shadow web is nearly guaranteed to be an urban legend about a net deeper than the darknet that contains even more illegal stuff. The easiest way to access the dark web is to download a Tor browser and then access the Tor Network.
- With the Deep Web, if you’re accessing personal accounts or sensitive data, the primary risks are related to security and privacy breaches.
- It is an encrypted network built on top of the existing internet, and specific software or tools are required to access the darknet.
- It is even possible to illegally download movies, music, and other digital media without paying for it.
- From a regulatory perspective, the Deep Web aligns with mandates like GDPR, which demand controlled data environments.
- Similarly, logging on to the Tor browser in order to browse the dark web doesn’t mean you’re breaking any laws.
- Adopt platforms like SAGA® that automate deep web and dark web monitoring, offering filtered, incident-ready intelligence while reducing analyst exposure to harmful content.
The Deep Web Is Generally Safer And More Secure Than The Dark Web
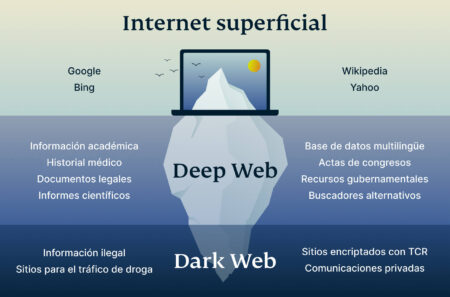
As with most things in life, in this debate, too, there are enough shades of gray; some just happen to be darker than others. The single-largest chunk of the Deep Web actually consists of statistics and databases, with U.S. Government agencies, like the National Oceanic and Atmospheric Administration, NASA, the USPTO and the SEC accounting for a large amount of the info. There are also millions of pages that lie on the ‘intranet’, which are internal networks of organizations and are accessible only by people admitted into the system by the administrators. At the moment, the Dark Web is defined as a layer of information and pages that you can only get access to through so-called “overlay networks”, which run on top of the normal internet and obscure access.
Presenting applications of our technologies in the industrial sector. Highlighting the use of our products and services in educational institutions. Differentiate your business from competitors with secured Microsoft solutions. Privacy and security work differently in each one, and it’s important to know what to expect. In other words, the Deep Web is everything you use daily but isn’t open to the public.
Is It Legal To Browse The Dark Web?
Whether you’re browsing the surface web, the deep web or the dark web, Hancock said the same advice applies — proceed with caution. Using dark web browsers like Tor is legal in most countries, but accessing illegal content or services remains unlawful regardless of the technology used. Organizations should establish clear policies governing the acceptable use of anonymizing technologies by employees. The Deep Web’s design prioritizes privacy, inherently limiting accessibility. Content remains invisible to search engines, requiring users to possess specific credentials or URLs.
The Main Differences Between The Dark Web & The Deep Web
We can’t discuss the history of the dark web without understanding the history of TOR, the most popular dark web network. The principle of ‘onion routing’, which underpins TOR, was developed by the researchers Paul Syverson, Michael G. Reed and David Goldschlag at the United States Naval Research Laboratory in the 1990’s. The very first version of Tor, named ‘The Onion Routing Project’ or simply TOR Project, was developed by Roger Dingledine and Nick Mathewson. Since this turmoil, management and oversight of the software powering the largest dark web network has been fairly stable and consistent. But even beyond the technical complexities of the internet, the essence of the surface web can be difficult to grasp.
Security Risks
This includes websites, blogs, online product listings, and even public posts on social media. The dark web’s anonymity draws users who need private communication, want to share sensitive information, or seek access to content censored in certain regions. But while it can support legitimate uses such as whistleblowing or journalistic sources, it’s also a hub for illegal activity. Criminals use it to buy and sell stolen data, commit identity theft, or conduct illicit transactions.
How Pipeline Protects
This includes content behind paywalls, subscription services, password-protected pages, email inboxes, and even private social media accounts. The deep web is essentially the part of the internet that is not indexed by search engines like Google or Bing. This vast segment includes private databases, academic resources, and government records. Access to the deep web typically requires specific credentials, such as usernames and passwords, which makes it a haven for sensitive information like medical records and confidential corporate data. The Deep Web contains all the web sites that web crawlers cannot index. Examples of sites on the Deep Web that require a login to access include bank accounts, Netflix accounts, and social media accounts.
Access This Chapter
While it protects your identity, it can also expose you to interactions with dangerous threat actors. Understanding the difference can help you avoid potential risks and stay secure online. The risks of accessing the deep web vs. the dark web may be similar but not exactly the same. Most of this limited collection is in the form of Google sites and services. In reality, the internet is enormous, and it has around one billion websites existing on servers around the globe.
So they’re right there on the internet, but you can’t find them by doing a quick search. While it may come as a surprise to some, about 7,500 terabytes of all the information on the internet is on the deep web, compared to only 19 terabytes on the surface web. Surfing the hidden internet brings us face-to-face with the dark side of the internet.
Key Differences Between The Dark And Deep Web

While the deep web is chiefly used for legitimate day-to-day online activities, the dark web is mainly anonymous and known as a haven for conducting illegal transactions. If the dark web lets users anonymously engage in illegal or dangerous activity, why does the government allow it to stay up and running? There isn’t any one way to access the deep web — it just depends on what you’re looking for. You need passwords to access your work email, or you’ll need to follow an internal link to find the right shirt to buy for an event. It takes more effort to access, but it doesn’t require the same level of legwork that accessing the dark web needs. Therefore, although it’s not illegal to just access the dark web, it makes you one of a kind.
Now, Let’s Understand The Difference Between The Deep Web And Dark Web
Law enforcement routinely shuts down and prosecutes sites and people doing illegal things on the Dark Web. However, these risks are similar to those on the surface web and the solution are the normal cybersecurity practices (secure connections, Multi-Factor Authentication, password managers, etc.). The darknets it operates on aren’t usually accessible via regular browsers – as we said, the Tor Network requires the Tor Browser. If your Social Security number is found on the dark web, take immediate action to protect yourself. Place a credit freeze or lock on your credit reports, monitor your credit reports and financial accounts closely for any unauthorized activity, and consider enrolling in a credit monitoring service. Additionally, contact the Social Security Administration to report the breach and discuss further protective measures.
It contains 7,500 terabytes of information, compared to only 19 terabytes of information in the “surface” web. To look at it differently, it makes up between 90% and 95% of the internet. Although the Dark Web is often used for illegal activities, it’s not illegal to access it in many countries. Some people use the Dark Web for legitimate reasons, but prefer to remain anonymous. There are many clear, deep, and dark web sites, forums and marketplaces where threat actors can access victims’ online accounts.



