
For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography. Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. Some markets even sell privacy tools, but you are more likely to run across counterfeit prescription pills and stolen identities. You only need to upload your PGP key or let the platform create one. Use it to link your GitHub account, Twitter, Bitcoin address, and Facebook. This .onion link makes it impossible for hackers to impersonate your profile.
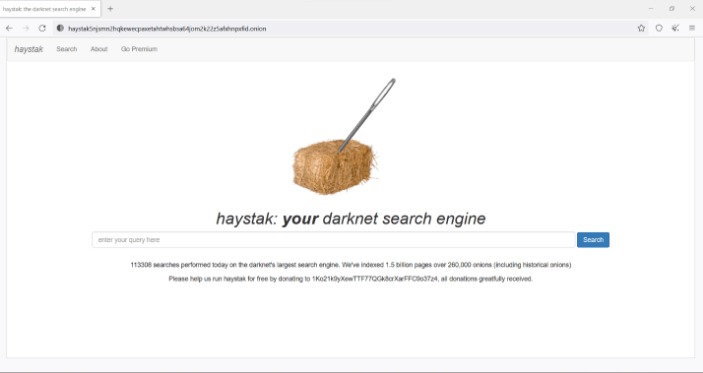
Ruheni Mathenge specializes in writing long-form content dedicated to helping individuals and businesses navigate and understand the constantly evolving online security and web freedom worlds. His articles have appeared in many respected technology publications. Dark web forums are online platforms that can only be accessed using anonymous networks, mainly Tor…. However, most are outdated and have not kept up with the changing landscape. For example, DuckDuckGo is the most popular but often shows repetitive results and is sometimes unrelated to the question.
Tips For Safe Browsing:
For example, it maintains your privacy and enables you to access untraceable content and services. These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data. Keep in mind that you’ve to use very specific keywords when searching. And most importantly, be patient as you’ve to sort through a lot of useless results. These search engines work best if you already know what site you’re looking for, not for general browsing.
Dark Web News And Media
Anyway, if you’re in this sort of thing, someone can help you get inside a Facebook account for 250 euros. It goes without saying that I do not advise you to seek this sort of service. These domain names are not registered with a central authority but are instead derived from cryptographic keys. Offering books for free, shadow libraries face the morality question of copyright vs. access to information and knowledge.
While you don’t need to log in to access any of the dark web links listed here, you can’t find them with a search engine like Google. The only way to access the dark web is by using the correct browser and knowing the URLs of the pages you want to visit. Scroll on to learn more about dark web links (also called Tor links or onion sites), get the right links for some of the best Tor sites, and find out how to visit them safely. Most advanced users advocate removing VPN services in order to reduce delays and improve flexibility.
Continued Popularity Of Black Traffic Schemes
Although the Tor browser has sufficient encryption, combining it with a VPN offers better protection. However, you should not see it as an opportunity to engage in illegal activities to avoid trouble with authorities. Your online activity and communications remain private and secret on the dark web. Because of this, some people use it to get around government restrictions, while others use it for illegal activities like smuggling drugs and weapons. With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential.

Dark Web Links For Software Downloads
With encrypted messaging, trusted vendor ranks, and a minimalist, no-nonsense interface, Anubis stands as a quiet but powerful force in the darknet world. WeTheNorth is a rising darknet marketplace known for its bold presence and community-driven philosophy. Built with resilience in mind, it offers secure transactions, transparent vendor systems, and support for major cryptocurrencies.
How To Access onion Sites Safely
My tests showed reliable performance for smaller files, but larger transfers can be slow due to Tor’s limitations. Pitch is a dark web-based Twitter/X alternative, providing a secure platform for anonymous discussions and information sharing. Unlike many dark web platforms, it maintains strict content guidelines while protecting user privacy.
The Rise Of Malicious AI

Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites. Unlike other search engines, it does not collect or share web activities and personal data of users. DarkMatter is a darknet marketplace built for those who demand both power and discretion.
- Infostealer threat actors specialize in malware that harvests personal data without consent, such as login credentials, bank accounts, and social security numbers.
- Since you cannot access a library of dark web links using the regular Internet, you can check out platforms dedicated to indexing these sites, like The Hidden Wiki.
- Some are looking for illegal stuff they can’t buy elsewhere, like drugs or counterfeit documents.
- Accessing it through an onion link is much more convenient if you’re unable to directly view it on your screen.
- However, The Wayback Machine allows website owners to block their sites from being archived, while archive.today does not.
That is why we emphasize caution, vigilance, and adherence to best security practices when exploring these hidden corners of the internet. Dark.fail has become one of the most trusted alternatives to the traditional Hidden Wiki. This directory focuses on providing users with verified, frequently updated links to a broad range of dark web services, including marketplaces, forums, and whistleblower platforms. Its community-driven verification system helps minimize the risk of scams and outdated URLs. Dark.fail also emphasizes user security by offering warnings about phishing sites and scam links.

This includes military-grade 256-bit encryption reinforced with a 2048-bit DH key and SHA2-384 authentication to ensure your traffic arrives at its destination safely. This adds extra protection since opening Tor itself encrypts your traffic. A virtual private network (VPN) is a good way to mask Tor activities. It adds an extra encryption layer and passes your traffic through a secondary server of your choice, preventing anyone from seeing that you are accessing the web via Tor. For this reason, you must watch out and avoid opening anything that looks suspicious to you. Immediately close your entire Tor Browser window (not just that active tab).
This means you have to know someone who is already using the platform. Even without the code, you can visit the security section to get tips on improving your daily life privacy. In most cases, whistleblowers have sensitive information about the government or a company. They can be easily traced and even prosecuted if they share the information on the surface web.
Stay Within Legal Boundaries
These can include the previously mentioned illegal offerings, but can also include ultra-private information designed to be shared only with certain parties. The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites. In 2002 the dark web began to grow significantly when researchers backed by the U.S.



