
Sites on the dark web use .onion domains, which are only accessible via the Tor browser. The Tor network adds a layer of anonymity, which helps dark web sites remain hidden and makes it impossible for conventional search engines to index them. The dark web contains content that’s only accessible through networks like Tor. Tor browsers create encrypted entry points and pathways for the user, so dark web activity remains anonymous.
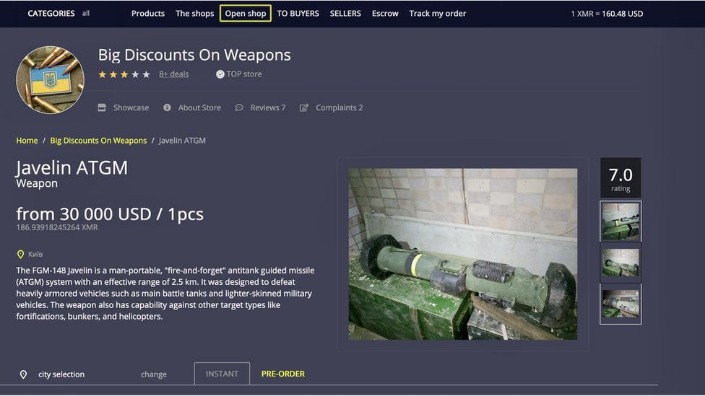
Altenen: A Credit Card Fraud Marketplace
ProPublica is a journalism outlet that has its own dark web version of its site. ProPublica’s work is all legal, so the .onion website isn’t much different from what you would find online. However, the main difference is that accessing it via a Tor browser gives you a layer of anonymity and security. DuckDuckGo is a private internet search engine available on the open web and as a Google Chrome extension.
Dark Web Phishing Kits: How Hackers Sell Ready-Made Scams
Dark web surveillance involves monitoring information on the darknet, such as to identify compromised credentials being sold, or to track forums to anticipate (and prevent) cyberattacks. State-sponsored threat actors are cybercriminal groups supported or directly managed by government agencies on the darkweb market. They often carry out attacks that align with their country’s political, economic, or military goals. Norton VPN fortifies your internet connection with ultra-secure AES-256 encryption, masks your IP, and never logs your activity. Exploring the dark web can be eye-opening, but it’s also risky without the right protection. While the Tor browser boosts privacy, pairing it with a VPN adds a critical layer of security.
Final Takeaway: Be Smart, Stay Safe
The surface web refers to everything you can access using search engines like Google, Bing, or DuckDuckGo — think news sites, social media platforms, and blogs. The deep web includes content that isn’t indexed by search engines, such as private databases, academic journals, medical records, or anything behind a login page. The dark web, however, is a small, intentionally hidden part of the deep web that requires special tools like the Tor Browser to access.
Law Enforcement Operations:
Your personal data & privacy is important to us & will never share your information with 3rd parties. Tor Browser is a technology that bounces internet users’ traffic through relays run by thousands of volunteers worldwide. This makes it extremely hard for anyone to identify the source of the information or the user’s location. Not only that, but they also have information concerning your calendar invites, travel information and meetings. Plus, some (such as Google) will automatically enter this information straight from your inbox. The site uses the anonymity of the Tor network to facilitate communication between whistleblowers, journalists, and news organizations, such as The Guardian.
How To Access Dark Web Websites
Malicious employees can steal company information and sell it on the dark net. A study shows around 83% of businesses reported at least one insider attack last year and the same study shows that the insider attacks will continue to grow in 2025. Criminals on the dark net use different types of malware to attack their victims’ devices. It was quite popular in the previous year and the trends show that it would be more popular in the current year.
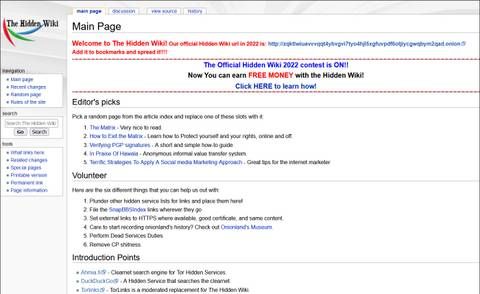
In addition, it doesn’t create user profiles based on browsing history meaning that you won’t be seeing personalized ads or search results while using it. In addition to useful information, The Hidden Wiki contains links to dangerous sites and marketplaces. Be sure to visit the original website and avoid malicious alternatives to safeguard your online data. The Hidden Wiki is a directory website with links to different Dark Web websites and resources similar to Wikipedia. The primary technology used to access the Dark Web is the Tor network, which allows users to maintain anonymity and privacy while accessing websites and services.
OnionName — Buy Readable Onion Domains
In 2021, they showed how tax rates benefit the rich, and they relied on stolen or leaked IRS documents to do so. In addition to the surface web, ProPublica also hosts their site on the dark web, because they want to make sure that everyone can access their reporting. The dark web, on the other hand, is a small part of the deep web that requires special tools like the Tor browser to access. Social media and gaming platforms are increasingly being used to recruit inexperienced hackers, further expanding these gangs’ reach. For example, Europol has warned the criminals will use coded messages and ‘gamification tactics’ to encourage minors to commit crimes. In 2025, state-sponsored actors are expected to continue using the dark web for politically motivated cyberattacks.
Privacy Advantages Of The Hidden Wiki
From timeless classics to modern works, the library provides a varied selection of reads for everyone. That said, if you’re mostly interested in open-access scientific research papers and academic articles, try Sci-Hub or Library Genesis (LibGen). ProtonMail, powered by Proton AG, provides end-to-end encryption to keep your email messages from being monitored.
Benefits Of Using WTN Market
Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal. Facebook’s dark web version allows users to access the site where it is banned or restricted. Although the social application is known for collecting data on its platform, it does not like sharing the information with others. Dark.fail is an easy-to-use .onion platform equipped with a status checker that tracks website uptime.

- Artificial Intelligence is all the buzz these days but unfortunately, the trend is the same on the dark net as well.
- It’s also a good idea to set up a VPN for an extra layer of protection.
- Furthermore, it’s critical to understand that Whonix is not a stand-alone browser.
- The Abacus Market links to the new dark web marketplace sections and took over much of the vacuum left by the AlphaBay takedown.
- Always verify .onion links through trusted directories like the Hidden Wiki or reputable forums.
Basically, if a Tor IP leak occurs before you connect to the VPN, your real IP address will be exposed. But if you connect to the VPN before connecting to Tor and an IP leak occurs, only the VPN’s IP address will be exposed. It’s also a playground for cybercriminals, illegal activities, and shady stuff. In addition to these tools, you need to exercise extreme caution when browsing on the dark web because there are tons of phishing and malicious sites on there. Only use .onion links that come from legitimate sources like The Hidden Wiki.
The BBC Tor Mirror is a testament to the fact that there are some very good websites on the darknet as well. The BBC site on the dark net is the official dark net version of the British media house. Who live in areas where the government firewall has banned access to news and authentic media sites. Like ProPublica, this is another platform on the dark net that is not inherently malicious. You can think of it as Google but with a strong focus on privacy and that is what makes it an ideal search engine for the Tor network. As the name suggests the drainer services are those where criminals can drain the crypto wallets, bank accounts, and digital wallets.
The Hidden Wiki remains one of the most popular dark web directories, but it’s also the most frequently cloned. The original offers categorized .onion links, from forums to file-sharing tools. While many users begin their dark web journey here, caution is strongly advised. Only trust versions that are verified by uptime monitors or digitally signed by trusted sources to avoid dangerous clones full of fake sites and malware traps.



