These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data. Keep in mind that you’ve to use very specific keywords when searching. And most importantly, be patient as you’ve to sort through a lot of useless results.
Download Tor Browser
Here’s practical advice for building targeted search queries and safely navigating .onion websites. This is below the surface web and accounts for about 90% of all websites. This portion includes academic journals, private databases, and other content hidden from the public for various reasons. The dark web isn’t only about illegal activities; it is specially designed to provide maximum anonymity by making your connection private online through encrypted servers. While the dark web is famously known as an illegal platform for criminal activities, that’s not all about this part of the web.
- Radar Rundown Free firewall software allow privacy ethusuiasts to secure their network and block mal…
- Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people.
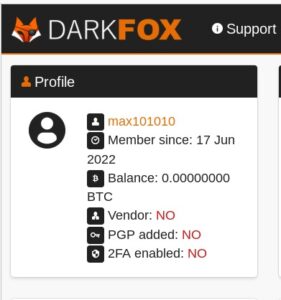
- You can buy credit card numbers, all manner of drugs, guns, counterfeit money, stolen subscription credentials, hacked Netflix accounts and software that helps you break into other people’s computers.
- Although ProtonMail also exists on the clear web, accessing it via Tor provides an extra layer of privacy if you don’t want to leave a trace of you even using ProtonMail.
- While the deep web includes legitimate, unindexed content such as private databases and subscription-only platforms, the dark web specifically facilitates anonymity.
Install And Update Security Software
Exploring the dark web can be eye-opening, but it’s also risky without the right protection. While the Tor browser boosts privacy, pairing it with a VPN adds a critical layer of security. Unfortunately, many dark web websites are devoted to the illegal trade of leaked personal information.
Is The Dark Web Illegal?
To further obscure transactions, Bitcoin users can employ digital currency exchanger services to convert their Bitcoin into online game currency, which can later be converted back into fiat currency. Services such as Tumblers are also available on the dark web to help hide transactions. However, Bitcoin’s relevance in the digital world has also made it a scam target. Law enforcement agencies frequently target sites that distribute child pornography. For Example, In May 2021, authorities in Germany brought down Boystown, a child pornography network with more than 400,000 registered users.

The Imperial Library currently holds around 1.5 million books, some of which may be hosted illegally, and thus, their consumption might violate copyright laws. To protect yourself against any legal repercussions, you should consider using NordVPN. Therefore, you will always find updated search results while using this service.
Popular Dark Web Search Engines
The dark web provides these groups with chat platforms to inspire terrorist attacks and ‘How-to’ guides to teach people how to become terrorists and hide their identities. There are reports of illegal services on the dark web, ranging from paid assassinations to the trafficking of sex and weapons. However, some of these alleged services, such as professional ‘hitmen,’ may be scams designed to defraud willing customers.
More On Tor Onions
Onion sites use The Onion Router (Tor) software to encrypt their connections and enable anonymous communication. The dark web is the unregulated part of the deep web, which encompasses all parts of the web not indexed by search engines. While the deep web comprises about 90% of the total web, the dark web makes up just a tiny fraction of the deep web total.
Law Enforcement Monitoring
Tor websites are located at this far end of the deep web, which are deemed the “dark web” and are only accessible by an anonymous browser. The Tor network provides powerful tools for enhancing online privacy and anonymity, but these benefits come with certain trade-offs. Haystak is often considered one of the deepest search engines for the dark web because it indexes around 1.5 billion dark web pages. While no search engine can cover the entire dark web due to its decentralized and ever-changing nature, Haystak is a top choice for exploring its hidden content. Yes, you can still be tracked on the dark web despite its privacy features.
Verification Through External Resources
The extra connection layers can act as a significant burden to your browsing experience if you’re doing something that is bandwidth intensive. As we mentioned above, when you connect to Tor your data first goes through an entry node, which can see your IP address. By connecting to a VPN before using Tor, you mask your real IP address before it reaches this entry node, adding an extra layer of security and anonymity. This means that using the dark web may attract attention from your ISP or even law enforcement.
Using a reliable VPN like ExpressVPN with dark web search engines is essential for protecting your privacy. It hides your IP address, encrypts your internet traffic, and prevents your activity from being traced. A VPN also masks your online behavior from ISPs, which could flag you as suspicious for accessing the dark web. This added layer of security keeps your identity hidden and shields you from online threats. The Open Web, also known as the surface web, constitutes the most accessible layer of the internet, readily navigated through popular search engines like Firefox, Google, Bing, and Yahoo.
While you’re at it, now might be a good time to check whether any of your personal information has been leaked on the dark web. SecureDrop uses Tor to provide a safe way for whistleblowers to contact various news outlets. Prominent organizations like The Guardian, The New York Times, and ProPublica have implemented it. The software requires two-factor authentication to receive what’s been uploaded by the whistleblower and allows two-way communication between the anonymous contact and the media outlet. Borderless news reporting and uncensored media are among the most important and practical uses for the dark web. Bypassing firewalls and other forms of geo-blocking helps people to access news websites and social media they normally wouldn’t be able to — and do so with less fear of recrimination.
Beacon Cybersecurity Newsletter
This article aims to shed light on the more constructive side of the dark web, guiding readers toward reputable resources and reliable information. We’ll cover the foundational principles of anonymity on networks like Tor, discuss how to navigate this hidden realm safely, and emphasize the importance of verifying sources. Throughout, we’ll stress the ethical and legal considerations that come with exploring these lesser-known platforms. This browser is the most suitable option for accessing the dark web, thanks to its multiple layers of encryption.