Some of these are well-known, established threats that circulate in this nook of the web. However, others may be taking advantage of the dark web’s reputation to trick users out of large sums of money. Also, some users on the dark web may attempt phishing scams to steal your identity or personal information for extortion. Some alleged services like the professional “hitmen” may just be scams designed to profit from willing customers. Reports have suggested the dark web offers many illegal services, from paid assassinations to trafficking for sex and weapons. Illegal drug marketplaces like the Silk Road have been hijacked for police surveillance in the past.
Related Articles From The Safe Browsing Section
These sites offer access to illegal streaming of pirated movies, TV shows, sports events, or other copyrighted content, often in high quality. These sites bypass copyright protection and may be accessed only on the Dark Web to avoid legal scrutiny. Infiltrations can put you at risk of monitoring for other types of activity as well. Evading government restrictions to explore new political ideologies can be an imprisonable offense in some countries. China uses what is known as the “Great Firewall” limit access to popular sites for this exact reason. The risk of being a visitor to this content could lead to being placed on a watchlist or immediate targeting for a jail sentence.
How To Safely Access The Dark Web With Tor — Step-by-Step Guide (
- Finally, you need to enter website addresses to access content on the dark web since you can’t browse by entering a search query as you can on the clear web.
- In August 2021, co‑founder “DeSnake” relaunched AlphaBay with a decentralized infrastructure and stricter vendor vetting.
- Tor Browser has since become a popular tool of journalists, activists, and others that may be subject to being monitored online.
- Additionally, forums facilitate the exchange of exploit kits and zero-day vulnerabilities, which can be weaponized before patches are released.
- Second, it allows you to access websites or services that block Tor but accept VPN traffic, such as streaming or banking sites.
Is due to the ever-evolving nature of the dark web — search engines there simply can’t keep up with the changes, often providing irrelevant or repetitive results. On iOS, the recommended option is Onion Browser, but due to Apple’s restrictions, it lacks full Tor functionality. To improve security on mobile, you should always use a smartphone VPN, disabling JavaScript, and avoiding sensitive activities on mobile. Most dark web sites are unregulated, which means that there are fewer mechanisms in place to prevent you from accidentally downloading malware. It’s a good idea to connect to a trusted VPN before you even open the Tor Browser to access the dark web.
BROADBAND SHOPPING GUIDE
However, note that the site only uses non-sensitive and public data for the metrics. The Tor Metrics is a good place to get more information about the Tor project. It collects data from the public Tor network and archives historical data of the Tor ecosystem.
Best VPNs To Access The Dark Web Safely
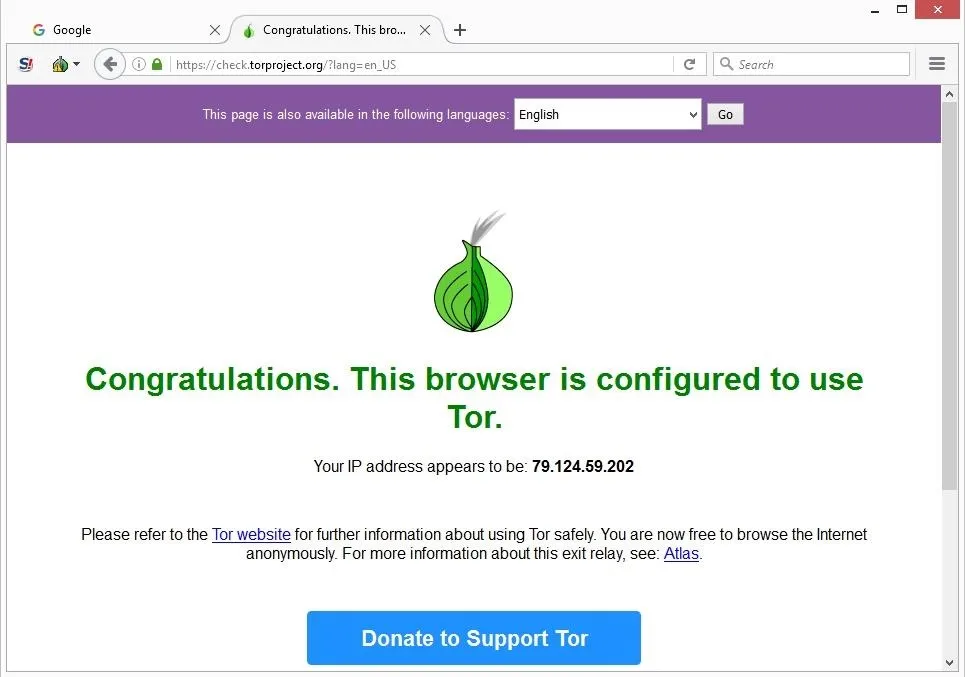
They can sometimes identify users through other methods, such as monitoring behavior, exploiting vulnerabilities or conducting undercover operations. The Tor Browser provides anonymity and privacy by routing your internet connection through a network of volunteer-operated servers around the world. This process, known as “onion routing,” masks your IP address and encrypts your data, making it difficult for anyone to trace your online activity. It’s simply a part of the internet designed to offer anonymity and privacy. While it does host illegal activities and shady content, it also supports legitimate uses like secure communication for activists, journalists, and whistleblowers in oppressive regimes. The dark web itself is neutral; how people use it is what makes it good or bad.
Sending Group Texts On Pixel 6: The Definitive Guide

Regardless of being a business, parent, or any other user of the web, you’ll want to take precautions to keep your information and private life off the dark web. With many Tor-based sites being overtaken by police authorities across the globe, there is a clear danger of becoming government target for simply visiting a dark website. The use of the dark web usually means that you are attempting to engage in activity that you could not otherwise carry out in the public eye.
If you have a legitimate or viable need to access the dark web, you’ll want to make sure you stay safe if you decide to use it. As such, the dark web has attracted many parties who would otherwise be endangered by revealing their identities online. Abuse and persecution victims, whistleblowers, and political dissidents have been frequent users of these hidden sites.
Some users, such as whistleblowers or journalists working on sensitive issues in oppressive authoritarian governments, need privacy to carry out their activities. More seriously, free VPNs – particularly those offered as standalone services – sometimes make money by selling your data to third parties. These aren’t the type of products you should use to keep you safe while exploring the dark web. The company may not have a large server network and access to much in the way of geo-restricted streaming content, but it does have plenty going for it in terms of privacy. You can sign up for the service completely anonymously, use a cryptographically signed installer, and double up on encryption using MultiHop servers. Surfshark is a low-cost provider that ticks all the boxes for use with the dark web.
How To Get On The Dark Web Safely & Anonymously In 2025?
Like I2P, it uses a distributed network database for added assurance against cyber attacks. However, you won’t be able to use I2P to access as many official dark web sites as Tor. Remember, the Tor browser connects to the internet differently than regular browsers in an attempt to increase your anonymity online. Using Tor is especially helpful in countries where authoritarian governments censor the internet, preventing citizens from accessing news outside their country.
PRIVACY ALERT: Websites You Visit Can Find Out Who You Are

Open the VPN app and connect to a nearby server before launching the Tor Browser, and that’s it! This ensures that your real IP address is hidden from the first Tor relay (it sees the IP address that your VPN provider supplies). Then the Tor anonymity network relays further obfuscate your true location, as the browser relays your browser traffic through several relay locations. A secure VPN server slows down your browsing much less than the Tor Browser and also opens access to geo-blocked local content around the globe.
Stay One Step Ahead – Protect Your Data From The Dark Web
However, it’s up to us to take control of our personal privacy in a world of bulk data collection, surveillance, and personalized ad tracking. First — and this is strongly recommended — you should install a Virtual Private Network (VPN). Also, you need to use a privacy-focused browser such as the Tor network to connect via nodes and proxy servers, which are more secure and aim to anonymize traffic requests. The Tor browser is able to access the special domain names, with the suffix .onion, used in the dark web.
- Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe.
- The US Naval Research Laboratory developed The Onion Routing (Tor) project in the late 90s.
- For example, China uses the Great Firewall to block access to Western sites.
- For example, randomly clicking a link can land you in extreme content, such as child pornography, which is a serious criminal offense to access.

Because traffic never leaves the Tor network, neither Internet service providers nor platform operators can easily trace the sender—crucial protection in sectors where retaliation is swift. There’s evidence that law enforcement agencies in freer countries operate many exit nodes for monitoring and surveillance purposes. This is because Tor traffic is usually unencrypted when it passes through the exit node. The Tor network’s principal benefit is that it routes your traffic through numerous servers, wrapping it in several layers of encryption.



